Mikrotik Site to Site Ipsec VPN
*Information on this page was taken directly from http://wiki.mikrotik.com/wiki/Manual:IP/IPsec. We did not create this document and do not take responsibility for any possible outcome of using these directions.
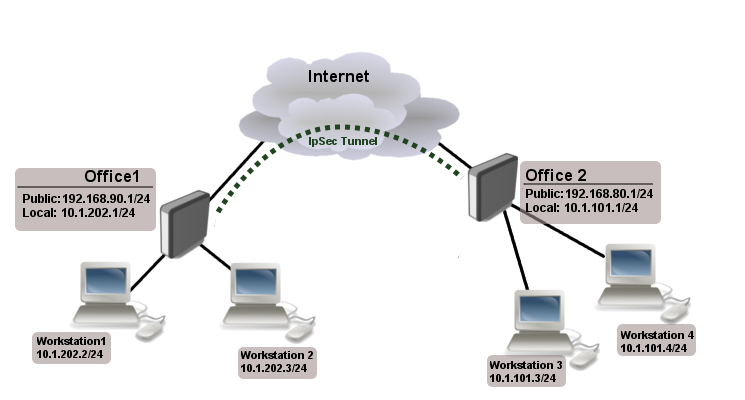
Site to Site IpSec Tunnel
Consider setup as illustrated below
Two remote office routers are connected to internet and office workstations behind routers are NATed. Each office has its own local subnet, 10.1.202.0/24 for Office1 and 10.1.101.0/24 for Office2. Both remote offices needs secure tunnel to local networks behind routers.
IP Connectivity
On both routers ether1 is used as wan port and ether2 is used to connect workstations. Also NAT rules are set tu masquerade local networks.
Office1 router:
/ip address add address=192.168.90.1/24 interface=ether1 add address=10.1.202.1/24 interface=ether2 /ip route add gateway=192.168.90.254 /ip firewall nat add chain=srcnat out-interface=ether1 action=masquerade
Office2 router:
/ip address add address=192.168.80.1/24 interface=ether1 add address=10.1.101.1/24 interface=ether2 /ip route add gateway=192.168.80.254 /ip firewall nat add chain=srcnat out-interface=ether1 action=masquerade
IpSec Peer's config
Next step is to add peer's configuration. We need to specify peers address and port and pre-shared-key. Other parameters are left to default values.
Office1 router:
/ip ipsec peer add address=192.168.80.1/32 port=500 auth-method=pre-shared-key secret="test"
Office2 router:
/ip ipsec peer add address=192.168.90.1/32 port=500 auth-method=pre-shared-key secret="test"
Policy and proposal
It is important that proposed authentication and encryption algorithms match on both routers. In this example we can use predefined "default" proposal
[admin@MikroTik] /ip ipsec proposal> print
Flags: X - disabled
0 name="default" auth-algorithms=sha1 enc-algorithms=3des lifetime=30m
pfs-group=modp1024
As we already have proposal as a next step we need correct IpSec policy. We want to encrypt traffic coming form 10.1.202.0/24 to 10.1.101.0/24 and vice versa.
Office1 router:
/ip ipsec policy add src-address=10.1.202.0/24 src-port=any dst-address=10.1.101.0/24 dst-port=any \ sa-src-address=192.168.90.1 sa-dst-address=192.168.80.1 \ tunnel=yes action=encrypt proposal=default
Office2 router:
/ip ipsec policy add src-address=10.1.101.0/24 src-port=any dst-address=10.1.202.0/24 dst-port=any \ sa-src-address=192.168.80.1 sa-dst-address=192.168.90.1 \ tunnel=yes action=encrypt proposal=default
Note that we configured tunnel mode instead of transport, as this is site to site encryption.
NAT Bypass
At this point if you will try to establish IpSec tunnel it will not work, packets will be rejected. This is because both routers have NAT rules that is changing source address after packet is encrypted. Remote router reiceves encrypted packet but is unable to decrypt it because source address do not match address specified in policy configuration. For more information see packet flow ipsec example.
To fix this we need to set up NAT bypass rule.
Office1 router:
/ip firewall nat add chain=srcnat action=accept place-before=0 \ src-address=10.1.202.0/24 dst-address=10.1.101.0/24
Office2 router:
/ip firewall nat add chain=srcnat action=accept place-before=0 \ src-address=10.1.101.0/24 dst-address=10.1.202.0/24
It is very important that bypass rule is placed at the top of all other NAT rules.
Related Articles
Mikrotik - Network Layout using Mikrotik & Firewall
**DISCLAIMER: The implementation described in this article has several pros and cons. It will help route VoIP traffic around an existing router or firewall that is conflicting with the VoIP service. It will also provide additional support tools like ...Mikrotik - Complete Setup Guide
**Disclaimer: This guide is provided by 3NG as a courtesy to its partners. You are using this guide at your own risk and 3NG is NOT responsible or liable for any issues that may occur from the use of this guide or a Mikrotik device. While we ...Mikrotik - Enabling Option 66
What is Option 66? Option 66 is a feature available in most commercial grade routers which enables offering a 'provisioning server address' to any device on the same LAN and obtaining an IP via DHCP. This method of "broadcasting" the server address ...Mikrotik - Change LAN Subnet
By default Mikrotik use the following LAN subnet, 192.168.88.0/24 with the gateway IP being 192.168.88.1. For this example the Mikrotik's subnet is being changed to 10.0.0.0/24 with a gateway IP of 10.0.0.1. There are six items that will be updated. ...Mikrotik - Configuring QoS
To configure QoS (Quality of Service) on a router successfully, you first need to know the speed that the internet circuit is consistently stable at. To find the stable speeds of the circuit, we recommend using an internet speed test, running it at ...